A long time ago, when Microsoft Entra ID was still called Azure Active Directory, and Microsoft 365 was known as Office 365, I managed a cloud migration for one of my customers. The objective was simple but ambitious: eliminate every on-premises server and fully embrace the cloud.
The Initial Migration
We started by migrating all endpoints to Azure Active Directory, while files and email were transitioned to Office 365. Device management, including both laptops and mobile phones, was handled by Microsoft Intune – a solution I really appreciated. Intune was easy to implement, with intuitive and reliable rules and compliance policies. One feature I particularly liked was conditional access, which allowed me to lock down access to SharePoint so that only company devices could connect. I also integrated Intune with Apple Business Manager for streamlined sign-ins.
To further enhance security on these devices, I implemented the following:
- XDR Endpoint Protection
- Data Leak Prevention
- DUO Multi-Factor Authentication
- BitLocker Encryption
Together, these measures ensured a high level of data protection.
Moving Remaining Systems to the Cloud
Once we had successfully migrated laptops and workstations to Azure AD and Office 365, it was time to move the remaining systems to the cloud. Unfortunately, the company couldn’t find any SaaS or PaaS solutions that met their needs, so they opted for an application that would be installed on Azure Virtual Machines (VMs).
However, there was a problem: this application didn’t integrate with Azure AD and instead used LDAP for its credentials repository. All users were in Azure AD, and synchronization was only one-way (from the local domain controller to Azure AD), not the other way around.
The Solution: Azure Active Directory Domain Services
Thankfully, Microsoft offered Azure Active Directory Domain Services (Azure ADDS), now rebranded as Microsoft Entra Domain Services. Azure ADDS is essentially Active Directory as a PaaS offering, where you don’t have to maintain domain controllers, yet you still get most of the functionality found in a traditional on-premises AD.
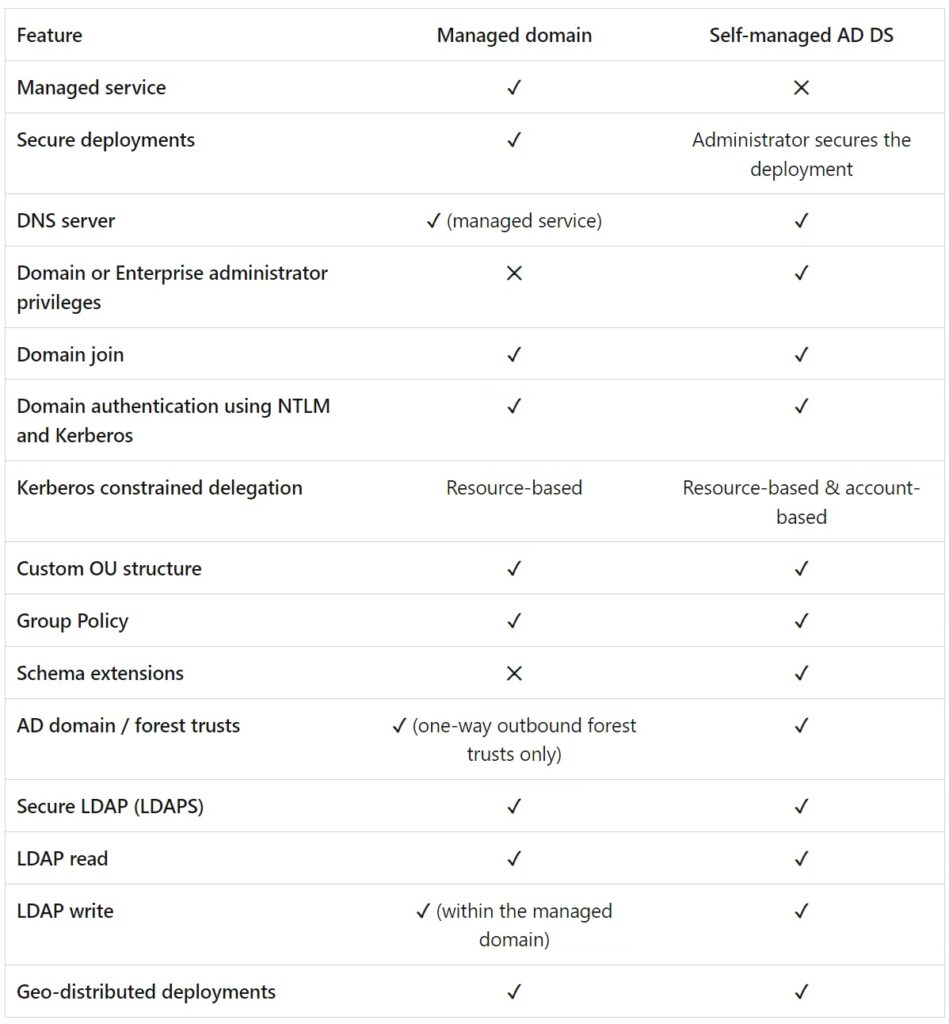
With Azure ADDS, we could synchronize Azure AD to Azure ADDS, allowing us to use LDAP for the application. Although it has been rebranded as Microsoft Entra Domain Services, the core product remains largely unchanged. It’s quite comparable to an on-premises domain controller, as illustrated in this comparison table.
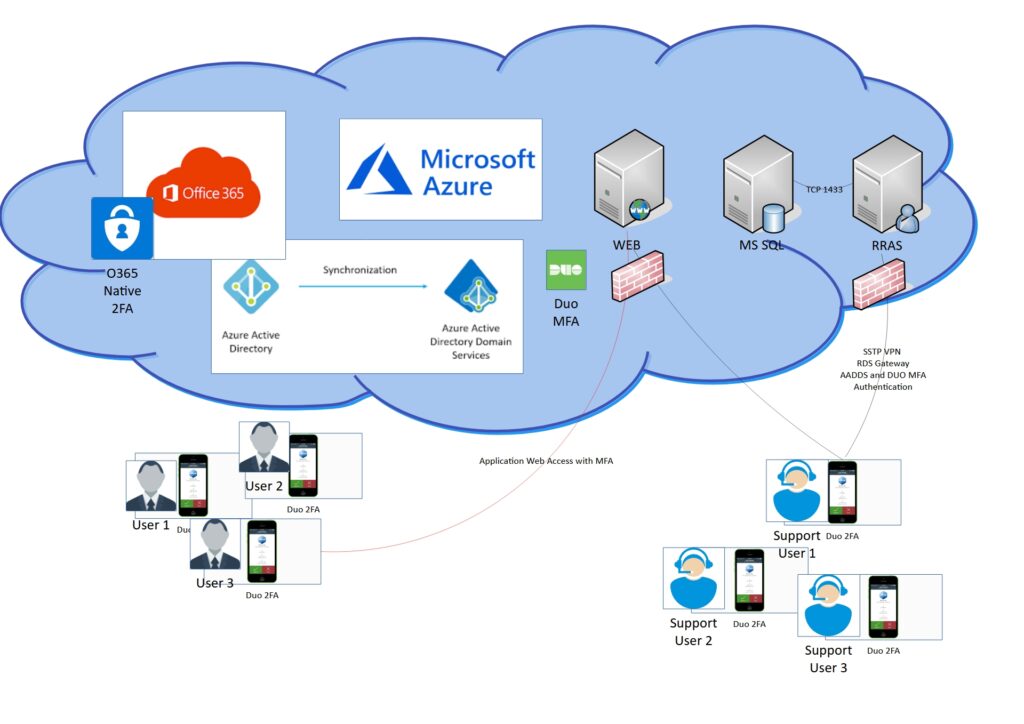
Securing Application Support Access
After setting up users in Azure ADDS, we created SQL and IIS virtual machines (VMs). The next challenge was securing access for the application’s support team. As is often the case, software vendors tend to prioritize functionality over security, and this one was no different. They asked for SQL port (TCP/1443) to be exposed over the internet with unencrypted traffic (since their application didn’t support encryption), and for shared RDP access to servers using a common username and password.
Clearly, this was unacceptable from a security standpoint. However, cost constraints forced me to think outside the box to create a secure, yet budget-friendly, solution.
An Innovative Approach
I decided to deploy B-series Azure Virtual Machines (BMs)—a cost-effective option—and set up Routing and Remote Access Service (RRAS) for VPN access, combined with Remote Desktop Services (RDS) Gateway for secure RDP. Although RRAS isn’t officially supported on Azure VMs, with some additional configuration, it worked well enough for this non-critical support access scenario.
To further strengthen security, I integrated DUO Multi-Factor Authentication (MFA) to ensure secure support access. Here’s a helpful guide on configuring RRAS on Azure VM, as well as another on setting up L2TP/SSTP client access.
Eliminating Shared Accounts
Since shared accounts present a significant security vulnerability, I ensured that each support and installation team member had their own individual user account. These accounts were created in Azure AD and synced to Azure ADDS, making the setup both secure and efficient.
The Final Design
In the end, the overall design was secure, cost-effective, and well-integrated with the company’s needs. It allowed for the flexibility of cloud infrastructure while providing strong security measures to protect company data and systems.